Sneaky methods for capturing the “Geolocation Flag(s)” for Hack.lu CTF
I decided that this post should could be summed up pretty quickly with just a few pictures, so I’m doing this in more of a blurb format than a blog post 
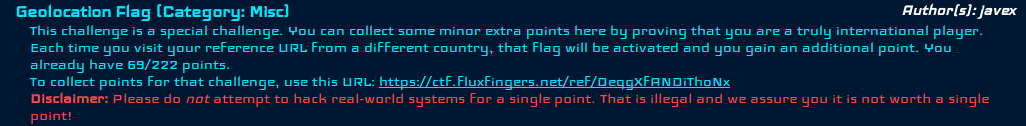
The challenge:
</p>
Pharming my blog readers (sorry about that)
#
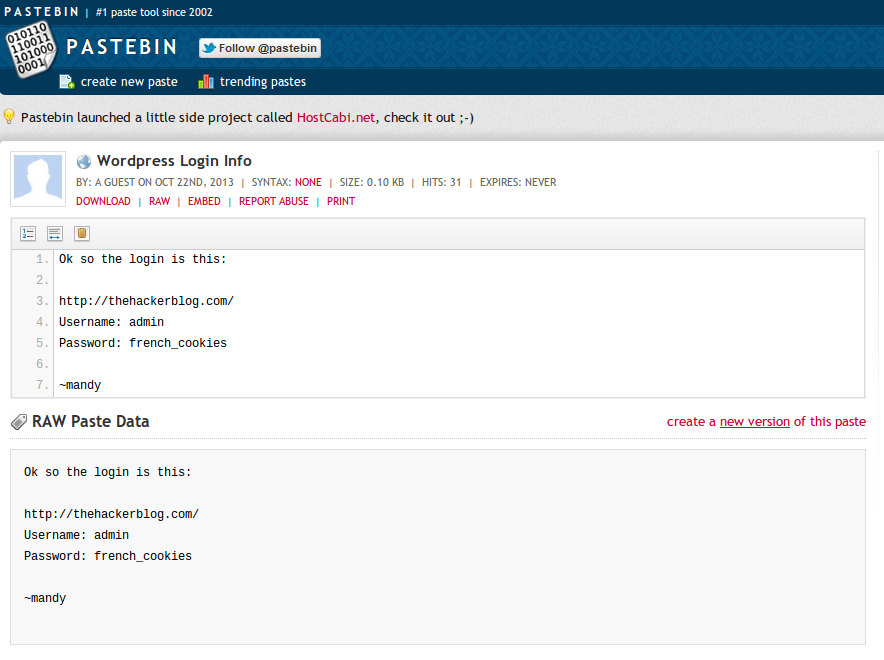
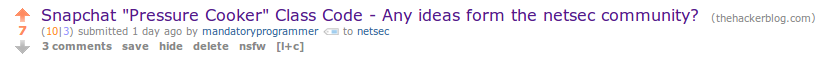
Luring people to my blog via Reddit posts and false Pastebin(s)
Creating a script to use all international TOR exit nodes
Mild amounts of proxy scraping
#
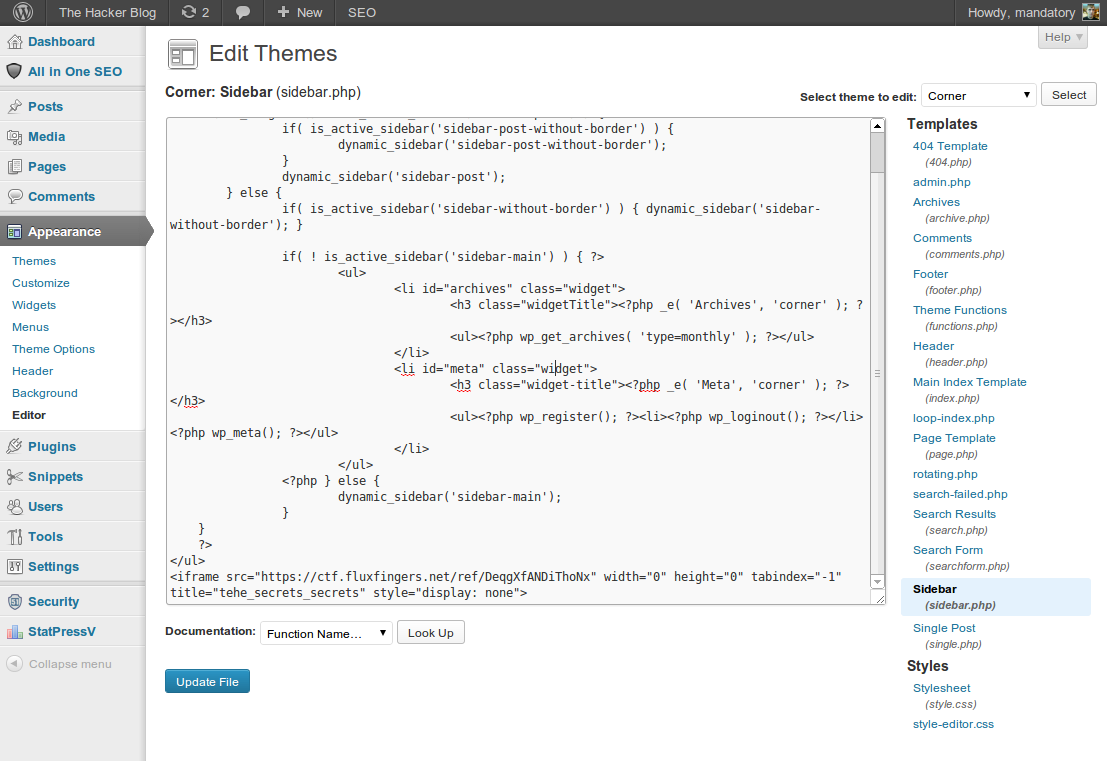
Making my forum signature image the “secret” link
(This works because the browser still does an automatic GET request for images, regardless of whether or not they are actually a proper image format). I ended up stirring up an international thread on the forum I used just to obtain more obscure country flags 😉
Again, sorry about farming you guys for flag points but their was no malware or anything – just a small bit of JSON!
Till next time,
-mandatory