xssless – Automatic XSS Payload Generator
After working with more and more complex Javascript payloads for XSS I realized that most of the work I was doing was unnecessary!
I scraped together some snippets from my Metafidv2 project and created “xssless”, an automated XSS payload generator. This tool is sure to save some time on more complex sites that make use of tons of CSRF tokens and other annoying tricks.
The XSS Vulnerability
Once you have your initial XSS vulnerability found you’re basically there! Now you can do evil things like session hijacking and much more!
But wait, what if the site is extra secure and locks you out if you use the same session token from a different IP address? Does this mean your newly found XSS is useless?
Of course not!
XSS Worms & JavaScript Payloads
Remember, if you can execute JavaScript in the user’s browser you can do anything the user’s browser can do. This means as long as you’re obeying same-domain, you’re good to go!
How?
JavaScript payloads of course!
Not only are JavaScript payloads real, they are quite dangerous – people often write-up XSS as being a ‘low priority’ issue in security. This is simply not true, I have to imagine this comes from a lack of amazement at the casual JavaScript popup alerts with session cookies as the message. Less we forget how powerful the Samy Worm was, propagating to over a million accounts and running MySpace’s servers into the ground. This was one of the first big displays of just how powerful XSS could be.
Building Complex Payloads
Building payloads can be a real pain, custom coding every POST/GET request and parsing CSRF tokens all while debugging to ensure it works.
After building a rather complex payload I realized this is pointless, why couldn’t a script do the same?
xssless
Work smart not hard, using xssless you can automatically generate payloads for any site quickly and efficiently.
xssless generates payloads from Burp proxy exported requests, meaning you do your web actions in the browser though Burp and then export them into xssless.
An Example Scenario
Image if we had an XSS in a site we wanted to compromise. You want to get a shell on this server but only employees/administrators can actually upload files. This server is also very secure and will lock you out if you change IP addresses so you can’t just steal the user’s token.
To start, we fire up Burp and set Firefox to use it as a proxy. Now we simply preform this web action in our test environment offline and upload a random file.
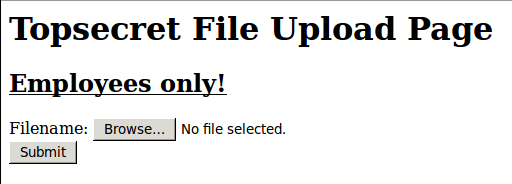
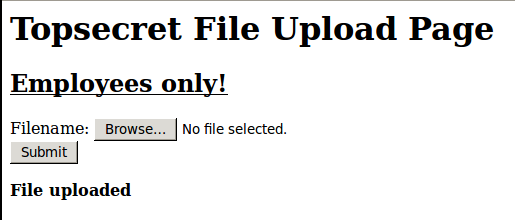
Select them in Burp and export them…
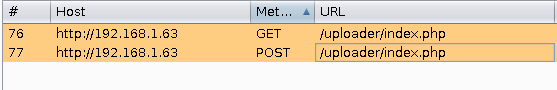
After selection, Right Click > Save items
And save them somewhere so we can access them.
Great, now we fire up xssless and generate our payload!
mandatorys-box% cat example_csrf_token_list.txt CSRFToken __VIEWSTATE csrf __RequestVerificationToken authenticity_token csrftoken mandatorys-box% cat example_file_list.txt file,/home/mandatory/Programming/C/hello_world mandatorys-box% ./xssless.py -s -f=example_file_list.txt -p=example_csrf_token_list.txt file_upload
The Output
Now, a few things have happened here.
-xssless has replaced the uploaded file with the shell specified in example_file_list.txt.
-The CSRF token named “csrftoken” has been automatically parsed due to the -p option specifying example_csrf_token_list.txt.
You now have a fully working payload that you can deploy against your target. Wasn’t that easy?
I’ll be adding more features as time goes on so please comment on any features you’d like to see!
Click Here for the Github Page
</a></center>