The Story of Bob and Mike, or How You Might Get Hacked By Sub Domain Brute Forcing!
Something that I’ve been really interested in is sub domain brute forcing, but what is it any why does it matter?
So, where to start? Let’s tell the story of a company system administrator and his journey.
So Bob (the sysadmin for a very important tech company) is put in charge of managing the DNS servers for H.U.E Inc among other things.
(For this story we’ll be using a 127.x.x.x format but we’ll pretend that these aren’t all loopback IP addresses)
Bob starts off by registering the domain name www.hueinc.com and points it to a server that hosts the company’s main website. So now whenever people go to www.hueinc.com it directs them to their web-server that serves up some static website detailing what the company is all about. We’ll say the IP address of this server is 127.0.2.1 just for example’s sake.
So, for those keeping track at home:
| DOMAIN | IP |
|---|---|
| www.hueinc.com | 127.0.2.1 |
| hueinc.com | 127.0.2.1 |
Great, but soon Bob is contacted by the developer department for H.U.E and they want a sub domain for their FTP server they setup. Easy enough, we’ll just set it to something easy to remember – after all this is what domains are for right? Bob decides that “ftp.hueinc.com” and “files.hueinc.com” seems like pretty easy-to-remember domains and set’s them to point twords the FTP server at the IP “127.0.2.8”.</p>
Cool, so now the company’s domain map looks like this:
| DOMAIN | IP |
|---|---|
| www.hueinc.com | 127.0.2.1 |
| hueinc.com | 127.0.2.1 |
| ftp.hueinc.com | 127.0.2.8 |
| files.hueinc.com | 127.0.2.8 |
Bob is now very confident with his ability to assign sub domains to things and starts assigning every department their own sub domains to make everything easier to use. He even sets up personal sub domains so he doesn’t have to remember all the annoying IP addresses of the server’s that he sometimes manages. The cPanel page that he uses to manage everything? Why that’s “cpanel.hueinc.com” of course! The company’s employee login page? “employees.hueinc.com”. The IP cameras for the building? “surveillance.hueinc.com”. The toaster in the lounge that tweets when bread is full toasted? “toasted.hueinc.com”!
Bob is very excited about how much easier he has made things!
So lets see, what’s the map look like now?
| DOMAIN | IP |
|---|---|
| www.hueinc.com | 127.0.2.1 |
| hueinc.com | 127.0.2.1 |
| ftp.hueinc.com | 127.0.2.8 |
| files.hueinc.com | 127.0.2.8 |
| cpanel.hueinc.com | 127.0.3.1 |
| employees.hueinc.com | 127.0.3.2 |
| surveillance.hueinc.com | 127.0.3.3 |
| toasted.hueinc.com | 127.0.2.9 |
| secret.hueinc.com | 127.1.3.1 |
| earth.hueinc.com | 127.2.1.2 |
| fire.hueinc.com | 127.2.1.3 |
| hercules.hueinc.com | 127.3.2.1 |
Etc, etc.
Wow, Bob certainly has been busy, what could possible go wrong here?
Meet Mike, he’s a Red Bull powered, not-so-ethical, insomniac. To top it all off he’s quite the computer security enthusiast and spends his time hacking at networks that he’s found an interest in. Sadly that system today turns out to be H.U.E. Inc.’s network.
Mike does a quick Whois on the domain name “hueinc.com” to start with and finds Bob’s contact details and the company’s phone number. Neat, so his opponent today is named Bob – let the games begin!
Mike now wants to know if they have any other systems than this static web server that shows the company’s details. After all, he is doubtful that he will have any luck hacking this server as most of the pages are just HTML files.
Perhaps this admin is new and has global DNS zone transfers enabled?
__A quick visit to https://tools.digitalpoint.com/zone-transfer and he discovers that they do not have global zone transfers allowed. (Mike prefers using this website as it won’t show his IP address for the query) A quick Google search reveals that only the company’s main website is indexed.
Oh well, I guess we’re doing this the fun way then!
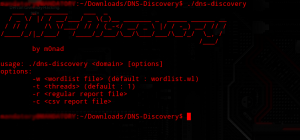
Mike loads up one of his favorite tools for this type of thing called “DNS Discovery“. He loves this tool because it’s multi-threaded and can be installed on many embed devices because of it being written completely in C.
He has a word list for sub domains that he’s been building up overtime and is quite happy with it, the game of profiling administrators is something he enjoys very much.
The interface for this tool looks something like this:
He lets the tool run it’s course, he finds that Bob is quite the sub domain wizard and has assigned quite a few sub domains to systems that should not be touched by people who aren’t employees!
Mike’s map of H.U.E. Inc. now looks something like this:
| DOMAIN | IP |
|---|---|
| www.hueinc.com | 127.0.2.1 |
| hueinc.com | 127.0.2.1 |
| ftp.hueinc.com | 127.0.2.8 |
| files.hueinc.com | 127.0.2.8 |
| cpanel.hueinc.com | 127.0.3.1 |
| employees.hueinc.com | 127.0.3.2 |
| secret.hueinc.com | 127.1.3.1 |
| fire.hueinc.com | 127.2.1.3 |
| hercules.hueinc.com | 127.8.2.2 |
His picture isn’t a very complete one but it reveals quite a few domains that he’s interested in.
Ah, sweet! Jackpot!
Mike isn’t quite done yet with his assessment yet however.
fire.hueinc.com? Does that mean the other “elements” are included as well?
Mike checks for “water.hueinc.com” and finds nothing, he then tries “earth.hueinc.com” and finds Bob’s other server as well!
Mike finds that many other sub domains all follow this sort of scheme, he discovers the “hercules.hueinc.com” sub domain as well and quickly scrapes a list of all of the greek gods for his word list. Sure enough, he enumerates ten more sub domains this way! He also now has an idea of some IP ranges the company might own and checks neighboring IPs for more systems. He finds a few more this way as well!
Mike has gone from having one static web server to attack to having tons of machines that he can mess with. Some of these systems were thought to be private and they probably haven’t been patched against the latest exploits.
What do _you _think Mike’s chances of success are now?
Is Bob and Mike’s story a unique one? This is probably not a common thing…right?
Sadly this isn’t a unique scenario at all, many (if not the majority) of system administrators will act exactly like Bob did. It isn’t that Bob didn’t know about the possibility of sub domain brute forcing but more that he never considered that anyone who do this. Heck, Bob even found the task of coming up with new sub domain names a fun job!
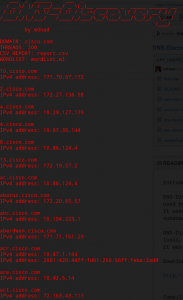
To close, here is a screenshot of this tool running against Cisco’s main domain name Cisco.com for five seconds (if this doesn’t get you a little freaked out I don’t know what would):
That’s a LOT of sub domains, I don’t even want to know what a full “scan” would yield…
EDIT: Just to clarify I’m not saying that companies shouldn’t use sub domains. My point was that this would be an effective way to enumerate systems that are scattered across different hosts (which is very possible, maybe you outsource you FTP etc.) A better point would be to just be cautious of how sub domains are assigned and not to depend on the obscurity of a system for security. This is well pointed out with the Cisco sub domains as many of those domains are _not _supposed to be globally accessible. I was hoping this post would get a few people to think about just what kinds of systems they consider “secret” that could be enumerated and attacked like this. Thanks for all the constructive comments so far – I believe I’ve fixed any errors in the post as pointed out by readers!
JUST FOR THE RECORD: I’m not endorsing the hacking of any of Cisco’s systems, I am merely pointing out the fact that this type of a thing happens all the time in real world networks. Cisco sadly has had a bad record when it comes to naming domains (they were vulnerable to zone-transfers for quite a while!). Please don’t attack any systems that do not belong to you! Jail time is not worth the adrenaline boost. Nuff said?