Stealing Lastpass Passwords With Clickjacking
LastPass, a popular password management service with addons for Firefox, Chrome, and Internet Explorer suffered from a clickjacking vulnerability which can be exploited on sites without the proper X-Frame-Options headers to steal passwords. The password auto-fill dialogue can be overlayed with a deceptive page to trick users into copying and then pasting their password into an attacker’s site.
Update: After disclosing with the Lastpass folks via their support system and getting a very quick and helpful response this issue is now fixed for all the latest versions of Lastpass on Chrome & Internet Explorer. Kudos to the Lastpass guys for being so quick on patching! The only patch that is not available is for Mozilla Firefox due to Mozilla’s unwillingness to approve the update in a reasonable amount of time. See below for full details.
For the proof of concept example we’ll use Tumblr, which makes use of JavaScript to prevent clickjacking. The protection is ineffective however, as the site can be framed with an HTML5 iframe sandbox to prevent the page from executing JavaScript:

While the page has been prevented from running JavaScript, the Lastpass addon is still able to add its auto-fill functionality to the Tumblr login form. Since this page can be iframed we can overlay an entire page to redress the UI in order to trick the user into clicking through the Lastpass dialogues. The following image shows this UI being redressed to look like a CAPTCHA system against bots:
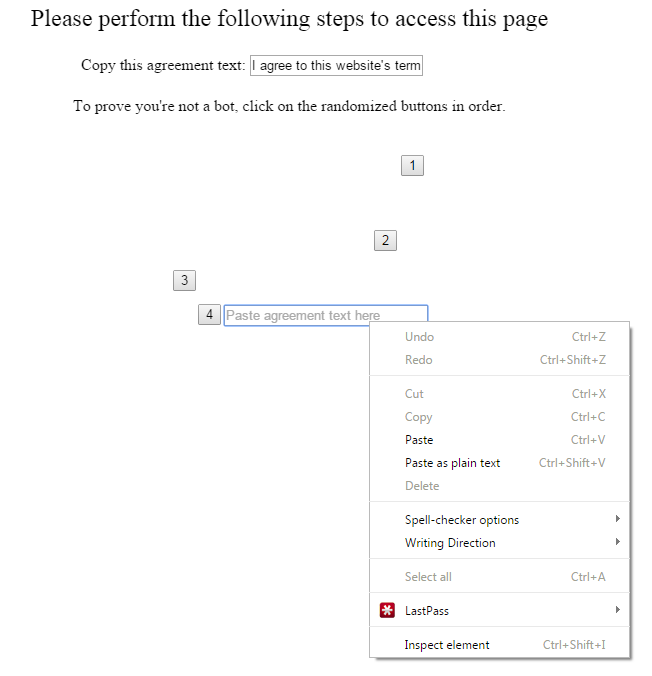
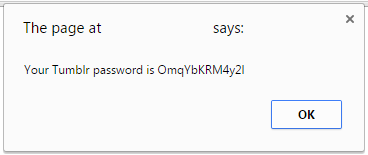
The user is prompted to copy the agreement text, followed by clicking on some “randomized buttons” before being asked to paste the agreement text back into a text box. What the user is unaware of is that they are actually copying their Lastpass password for Tumblr upon clicking button number three. When the user goes to paste the agreement text back into the website they are inadvertently giving away their password to the attacker’s site:
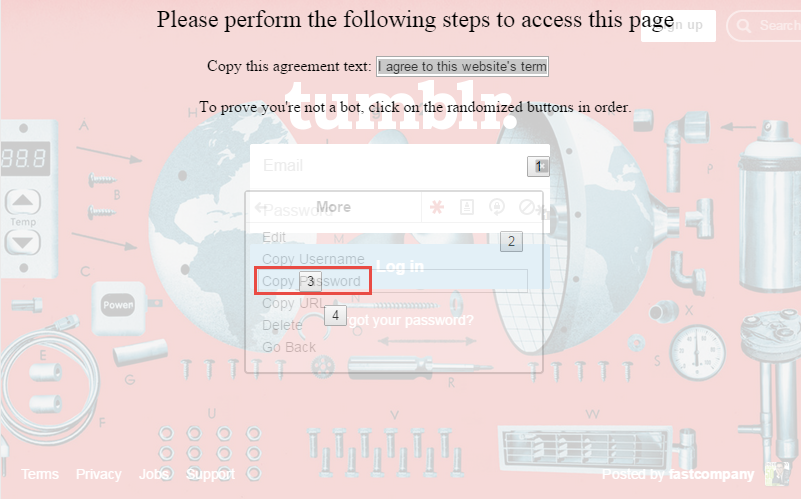
The trickery becomes obvious when the overlay is made slightly transparent:
If you’d like to test this out on your self, try the following link (please note this only works on the Chrome version of Lastpass):
EDIT: The above link no longer works due to Lastpass pushing a fix.
It goes without saying but the script does not actually log your Tumblr password – but you shouldn’t take my word for it.
A video demonstrating the vulnerability is also available here:
The fix for websites is possible by just using an X-Frame-Options: SAMEORIGIN header.
It would be trivial to build this exploit for other websites, please keep in mind that Tumblr has little to do with this issue – they are just the example. The core of the problem was with the Lastpass service.
Disclosure Timeline
- April 3, 2015 – Issue reported via the Lastpass ticket system
- April 4, 2015 – Lastpass responds with confirmation of this issue, confirms they will work on figuring out remediation. (Also discussing a mistake with the link I sent them showing the issue)
- April 20, 2015 – Patch implemented internally for testing before being pushed to production.
- April 22, 2015 – Path pushed to Chrome browser, other browser patches in the works.
- July 1, 2015 – Mozilla has still not pushed a patch out despite Lastpass submitting it on April 22nd.
The scariest part of this vulnerability has mainly been the fact the Mozilla has had time to review the patch for months and still hasn’t approved the patch. It’s worrying to think that security updates for Mozilla addons take months to reach users. It’s definitely changed my perspective on Firefox from a security perspective.
EDIT: I talked with someone who reviews addons for Mozilla and they shed some light on why the review took so long for the addon. It appears that the update was much more than just a fix for the clickjacking issue and due to the minified code for Lastpass it took a while to be reviewed. Additionally it appears that the urgency of the patch wasn’t clearly communicated to the Mozilla team. I apologize for the polarized view on the addon review process (a process that I am admittedly unfamiliar with). Overall a very nice explanation and it provided a nice amount of insight into the inner workings of that process.
Until next time,
-mandatory
