CSAW Lulz Writeup – Funny observations and serious problems
While everyone is preparing writeups for the cool challenges I think a lot of people would also be interested in the funny things that went on during CSAW.
Poor Kevin
One of the recon assignments was to find a hidden flag for “Kevin Chung”, the challenge simply starts like this:
What could possibly go wrong right?
Spoiler alert! Where you were supposed to end up was here: https://github.com/historypeats/putscan/commit/a31512af6e8f2ae76bce11c0bd363f899e3488d1
Which I didn’t exactly find out about right away – I did however find his website http://coderkevin.com/. This site initially taunted users about the key (via a Youtube video and some text) which brings us to the next point…
Being a judge and having public whois info for recon challenges is a REALLY bad idea.
Why?
People like me might get desperate enough for a key were I might actually just look you up and call you for the key. (http://www.networksolutions.com/whois/results.jsp?domain=coderkevin.com)
Which I did and the call went something like this (sorry Kevin, I can’t imagine your pain):
Me: “Hello?”
Kevin: “Is this about the whois info?!”
Me: “Oh…no…but if it was about that and if you did know a key…would the first letter be A?”
Kevin: *laughs* Oh god people have been calling me all day *hangs up*
So naturally, as satisfying as this was I am clearly not aware of social bounds so I decided to text him.
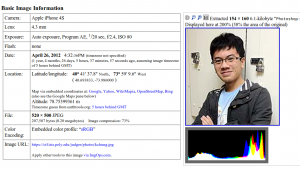
As if this wasn’t bad _enough _Kevin also forgot (or was not aware of) EXIF data.
So that’s horrifying, considering that search EXIF data is the exact thing _that you’d have to do to find a key.
_
TL;DR – Kevin is probably changing his number and address relatively soon. Also internet points are serious business!
Funny False Flag-ery
So I personally enjoyed the effort that people would put into having false flags. I encountered a few (and placed a few), it’s really all part of the game with CTFs though.
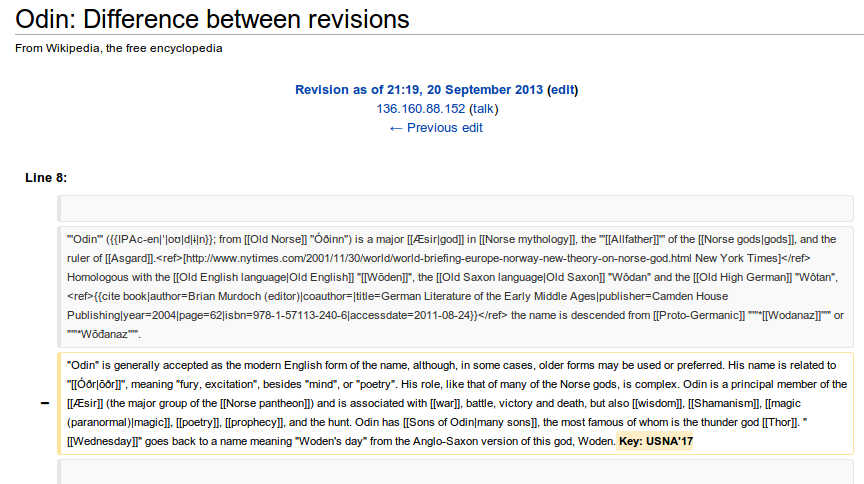
Exibit A – Wikipedia getting bombarded:**
It would appear that for a brief time someone managed to add a false flag to the Wikipedia article “Odin”, which was removed shortly afterwords. This one made it through and I have no idea if many more were being done to other Wikipedia articles (if you know of some please post it!) I find it hilarious that people would suddenly be bombarded will crap additions to pages because of some random CTF competition.
Here’s an image of this:
Exibit B – Widget False Flagging
Initially while doing the “widget” challenge for CSAW I thought the idea was to get the key by viewing someone else’s widget. This seemed reasonable enough unti I actually did it.
Just no so much crap and derping in those widget fields – people running Acunetix and false flags to throw you off were everywhere.
Luckily enough if you _did _want to see those entries I have some of them saved in a very screwed up format here: http://thehackerblog.com/downloads/internet_culture_gone_wild.txt
Please notice fabulous entries such as:
-
key{grep this bitch} (hehe, might've been me) -
"Please something" (I can taste the desperateness)
-
howlongcanyouhandleinsideofyouhowlongcanyouhandleinsideofyouhowlongcanyouhandleinsideofyouhowlongcanyouhandleinsideofyouhowlongcanyouhandleinsideofyouhowlongcanyouhandleinsideofyouhowlongcanyouhandleinsideofyouhowlongcanyouhandleinsideofyouhowlongcanyouha (Apparently about that long)
-
<script>alert("key{0ecb449efc3}")</script> (more false flagging) -
Widget: fuck Value: mygucciasswhole (HUNDREDS OF THESE, what the hell man?)
-
Change this to the value you want tested (Some time of automated software?)
Their are plenty more but those were some of the funnier values I found.
CSAW Actively Scanning our Browsers for Vulnerabilities
How many of you noticed that? Seriously it’s like right in the source and it does it pretty often.
Basically in every CSAW CTF page they had the following:
<script src=”http://browserscan.rapid7.com/EM-209038687/1/0/1/0/collect.js”></script>
The browserscan.rapid7.com homepage looks like this:
Nothing to sketchy right? Here’s an example scan of my browser.
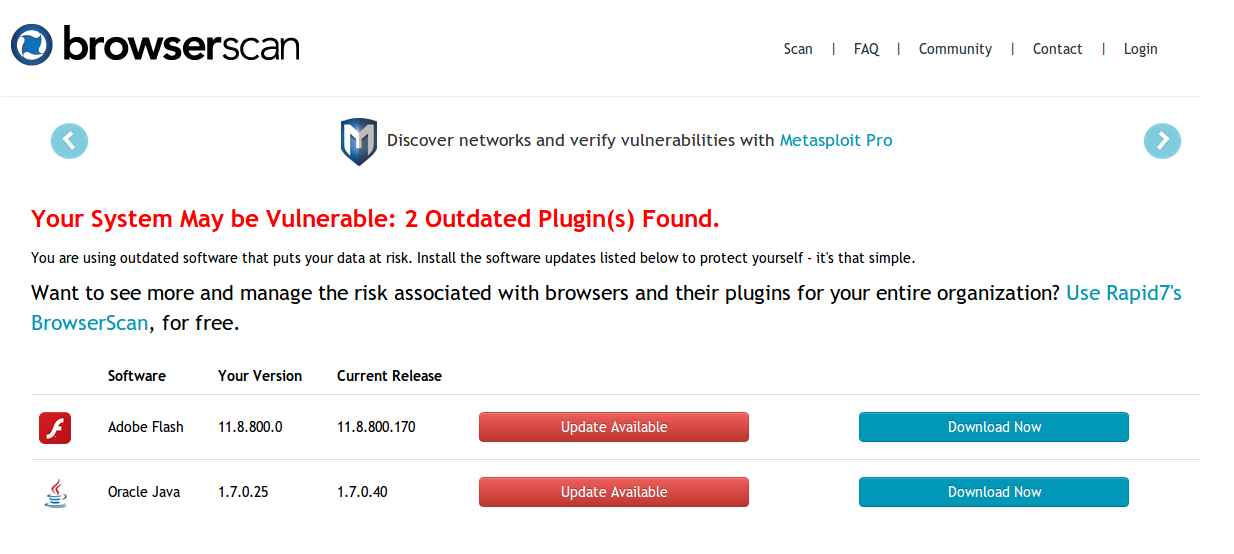
I really hope that this whole thing was just a way to hack a ton of CTF players but it really was probably more to gain lulzy statistics about players.
So that’s all I have for now but if I think of anything else funny I’ll add it – if you have anything funny to add please post it in the comments below!
This concludes the CSAW lulz writeup, I hope you learned something!
-mandatory