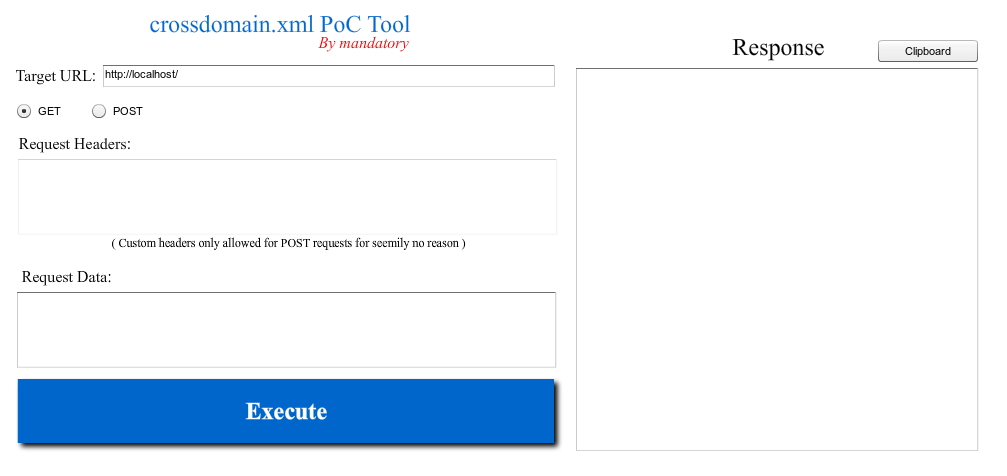
Crossdomain.xml Hacking – Proof of Concept Tool
After recently looking into how Adobe flash player does cross site requests I noticed that there was a shocking lack of tools to demonstrate crossdomain.xml insecurities. It seems like a pretty easy proof of concept to build so why isn’t there a tool to test this? Naturally I Googled around and couldn’t find anything so I decided to build my own over the weekend.
For those not familiar with Crossdomain.xml and how it applies to Flash/Adobe plugins…
Taken straight from Adobe’s website:
Why do you require a crossdomain.xml file?
A cross-domain policy file is an XML document that grants a web client, such as Adobe Flash Player or Adobe Acrobat (though not necessarily limited to these), permission to handle data across domains. When clients request content hosted on a particular source domain and that content make requests directed towards a domain other than its own, the remote domain needs to host a cross-domain policy file that grants access to the source domain, allowing the client to continue the transaction.
Source: http://www.adobe.com/devnet/adobe-media-server/articles/cross-domain-xml-for-streaming.html
To put it simply, the Adobe flash equivalent of Cross Origin Resource Sharing is accomplished by checking “http://yourdomain.com/crossdomain.xml” file for permissions.
So if you have a crossdomain.xml file that looks like this:
<cross-domain-policy>
<allow-access-from domain="*" />
</cross-domain-policy>
You are allowing any random domain to load a flash app which has permissions to do authenticated POST/GET requests on the clients behalf. So if they were logged into a site with a vulnerable crossdomain file they could potentially preform any action on behalf of the user (send money, messages, delete things, all sorts of stuff). It’s like a XSS vulnerability but with a flash requirement (not to make it sound unappealing or anything).
I also got the grand opportunity to discover Actionscript and all of it’s fun (missing) features. While trying to build a proof of concept I ran into a ridiculous amount of quirks – everything from not being able to read the response headers to not being able to send a POST request without body data (don’t worry it auto-converts the request to a GET for you). So, if the proof of concept is missing something (like the OPTIONS/DELETE/etc method) check to see if it’s not just an inadvertent HTML5 advertisement.
ANYWAYS, enough moaning!
Crossdomain.xml Proof of Concept Tool
If you know more than me about Actionscript (if you’ve spent more than a few hours on it you probably do) and see something missing from this tool – let me know and I’ll add it 
Permalink: //thehackerblog.com/crossdomain/
Till next time,
-mandatory